Overview
Discover how Evina's DCBprotect works
Evina's DCBprotect secures your Direct Carrier Billing
DCBprotect allows mobile network operators, payment gateways, digital merchants and ad networks to protect any payment flow, from the advertising banner to the payment confirmation page.
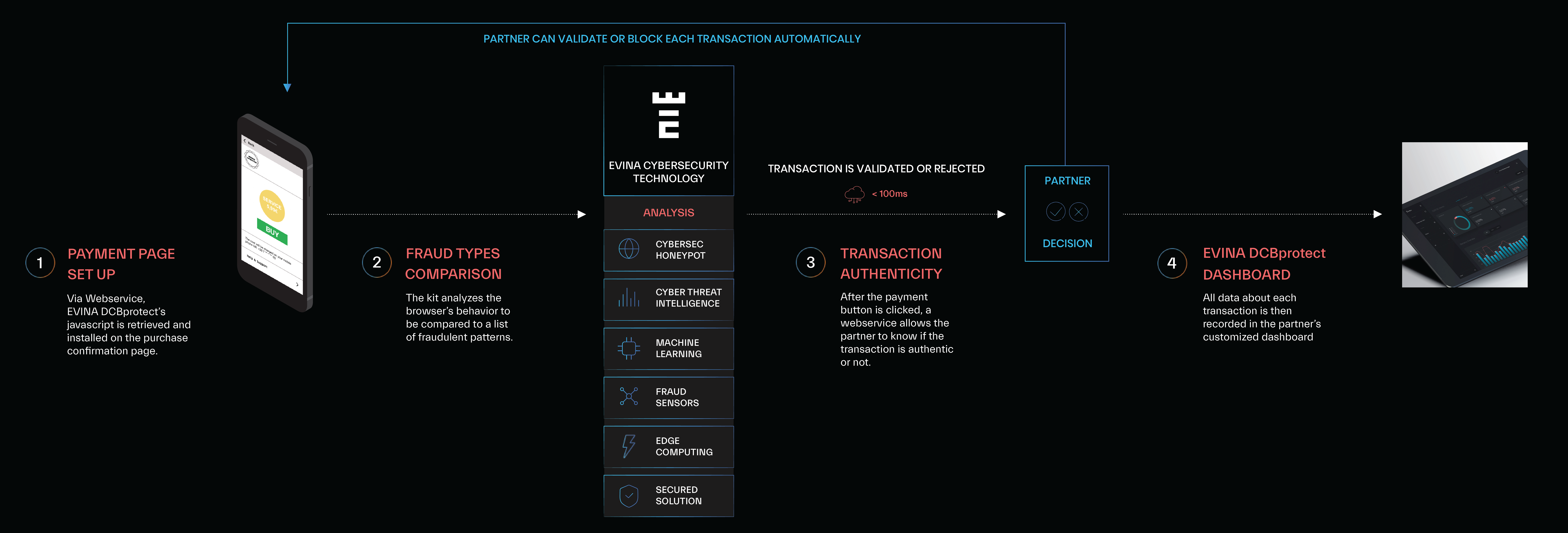
In addition to securing payment flows by detecting fraudulent transactions, DCBprotect:
- Ensures brand safety
- Decreases end-user complaint rates
- Eliminates fraudsters
- Optimizes conversion rates
- Opens traffic acquisition sources
Partners can focus on developing sustainable businesses with efficient payment flows and on building new partnerships while safely exploiting promising opportunities.
Evina supports partners on a daily basis by:
- Providing them with critical data on their traffic cost, efficiency and safety.
- Helping them ensure better purchase awareness, customer journey optimization and complaint management.
Most advanced fraud detection technology
Cybersecurity Honeypot:
Evina uses its own global mobile networks to attract fraudsters, reverse engineer their patterns and reinforce our solution.
Cyber Threat Intelligence:
A proactive approach on new fraud patterns and breach exploitation: we run Cyber Threat Intelligence involving in-depth analysis of threats from all sources, including the hidden ones in the dark web.
Machine Learning:
Data from millions of transactions analyzed every day is used to detect fraud patterns and block fraudulent payments.
Fraud Sensors:
The most advanced fraud sensors possible by constantly being at the forefront.
Edge Computing:
Cloud technology, data treatment & storage that is the closest to the end-user in order to have the best response time and bandwidth.
Secured Solution
Security is our priority, that’s why Evina’s technology always uses polymorphic encryption (encrypted algorithm) for the best possible data protection.
The best cybersecurity obsessions
- Best fraud protection possible (detection rate 99.7%)
- Fewest false positives (> 0.2%)
- Best latency (< 100ms)
No exclusions of any fraud types
DCBprotect detects all types of fraud activities and provides specific information relating to each transaction. Find the list of fraud types here.
GDPR compliant
DCBprotect does not store any personal data:
- No phone number
- No personal identifier
Evina is not considered a data controller or a data processor.
Data used, processed and stored during all flows are the minimum required to ensure the service functioning.
Dedicated dashboards
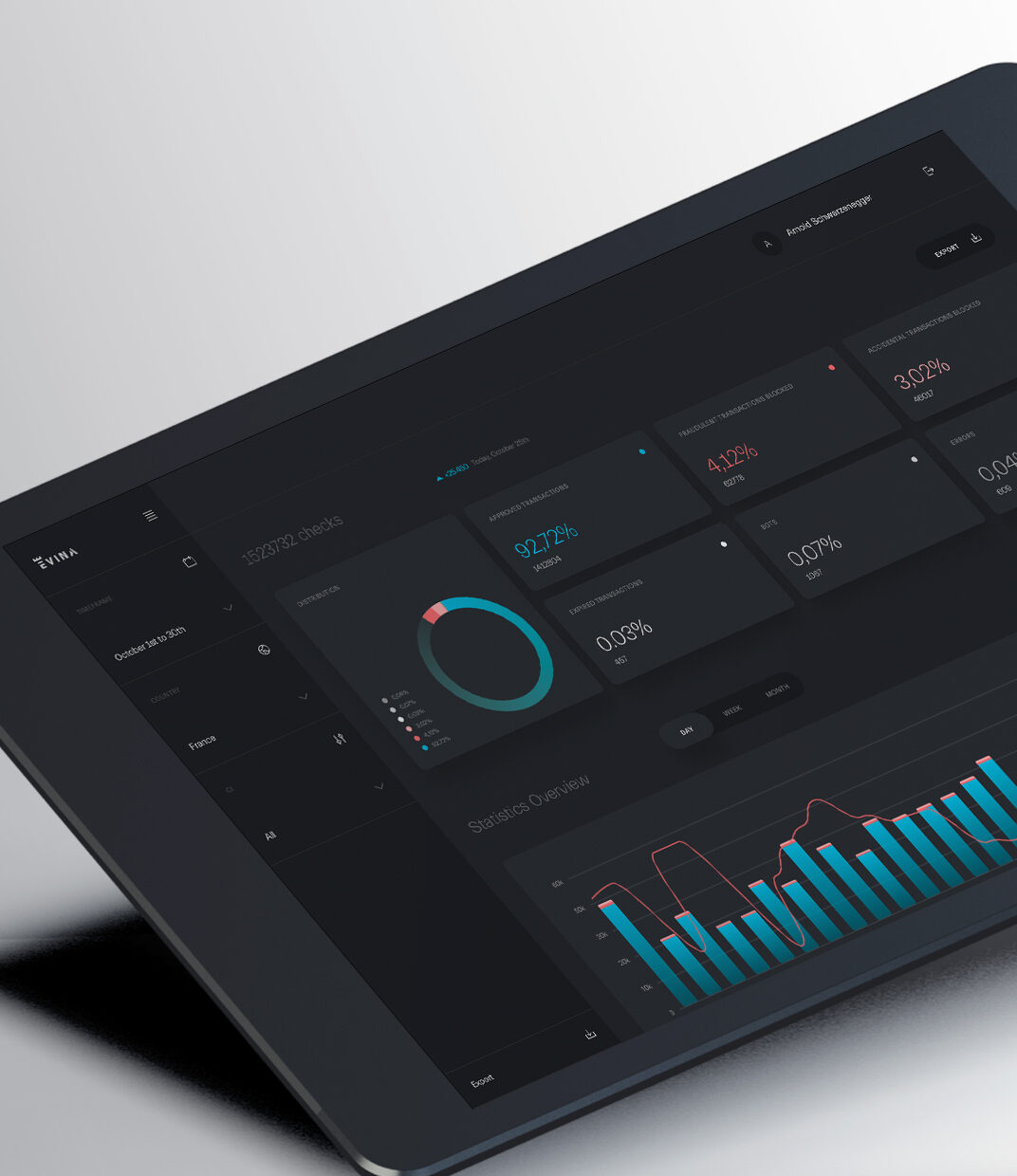
Evina provides partners with dashboards to monitor and see traffic analysis results:
- In real-time
- Dedicated personal access
- Training session
- Downloadable and shareable data
- Fully customizable data
- Customized alerts
In case of the Transparent Gateway integration
Only mobile network operators/payment gateways have access to the dashboard to monitor and analyze the traffic of their partners.
Updated about 3 years ago
